Introduction
The Well-Architected Framework (WAF) by Microsoft Azure provides a set of best practices to help you design and operate reliable, secure, efficient, and cost-effective cloud architectures. Whether you’re building a new application or migrating an existing one, applying WAF principles ensures that your solution is robust and future-proof.
In this guide, i’ll explore how to design a secure and scalable Azure architecture using WAF principles. I will cover both the theoretical foundations and a step-by-step tutorial to implement these principles in practice.
Part 1: Theoretical Foundations
- Security
Security is the cornerstone of any cloud architecture. Azure provides several tools to help you build a secure environment:
Azure Firewall: A managed, cloud-based network security service that protects your resources.
Network Security Groups (NSGs): Filter network traffic to and from Azure resources.
Azure Security Center: A unified security management system that strengthens your security posture.
Best Practices:
Implement Zero Trust Architecture.
Use Multi-Factor Authentication (MFA) and Conditional Access.
Regularly audit your security configurations with Azure Policy.

- Reliability
A reliable architecture ensures that your application remains available and resilient to failures. Key Azure services include:
Availability Zones: Protect your applications from datacenter-level failures.
Load Balancers: Distribute traffic evenly across resources.
Auto-Scaling: Automatically adjust resources based on demand.
Best Practices:
Design for high availability and disaster recovery.
Use Azure Site Recovery for backup and replication.
- Cost Optimization
Cost management is critical in the cloud. Azure provides tools to help you monitor and optimize your spending:
Azure Cost Management: Track and analyze your cloud spending.
Reserved Instances: Save costs by committing to long-term usage.
Best Practices:
Regularly review and optimize resource usage.
Use Azure Advisor for cost-saving recommendations.
- Operational Excellence
Operational excellence ensures that your architecture is easy to manage and monitor. Key tools include:
Azure Monitor: Collect and analyze telemetry data.
Log Analytics: Gain insights into your infrastructure.
Azure Policy: Enforce governance and compliance.
Best Practices:
Automate repetitive tasks with Azure Automation.
Use Infrastructure as Code (IaC) tools like Azure Bicep or Terraform.
- Performance Efficiency
Performance efficiency ensures that your application runs smoothly and efficiently. Key services include:
Azure CDN: Accelerate content delivery.
Redis Cache: Improve application performance with caching.
Best Practices:
Optimize database queries and use Azure SQL Database.
Use Azure Kubernetes Service (AKS) for container orchestration.
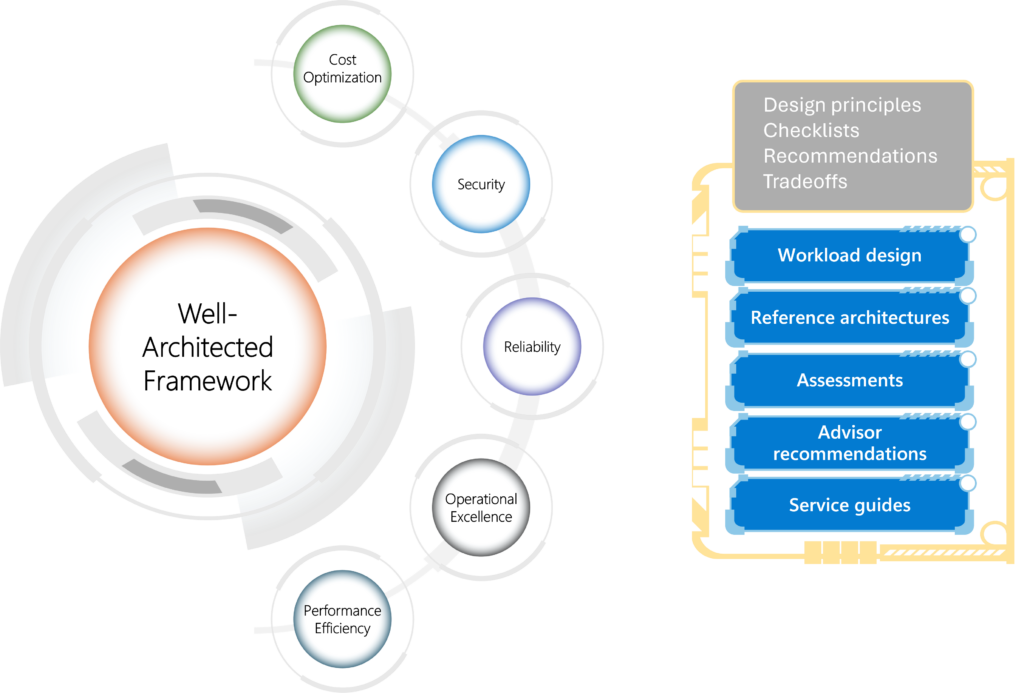
Part 2: Practical Implementation
Scenario: Building a Secure and Scalable Web Application
Let’s walk through the steps to build a secure and scalable web application using Azure services.
Step 1: Create a Resource Group and Virtual Network
Log in to the Azure Portal.
Create a new Resource Group.
Set up a Virtual Network (VNet) with subnets for different tiers (e.g., web, database).
Step 2: Deploy a Web App with Azure App Service
Create an Azure App Service for hosting your web application.
Configure Custom Domains and SSL Certificates.
Step 3: Set Up Azure Firewall and NSGs
Deploy an Azure Firewall to protect your VNet.
Configure NSGs to restrict traffic to and from your resources.
Step 4: Configure Azure Load Balancer and Auto-Scaling
Set up an Azure Load Balancer to distribute traffic.
Enable Auto-Scaling for your App Service Plan.
Step 5: Enable Azure Monitor and Log Analytics
Set up Azure Monitor to collect metrics and logs.
Use Log Analytics to create custom queries and alerts.
Step 6: Apply Azure Policy for Governance
Create Azure Policy definitions to enforce compliance.
Assign policies to your Resource Group.
Step 7: Optimize Costs with Azure Cost Management
Use Azure Cost Management to track spending.
Identify underutilized resources and take action.
Part 3: Conclusion
By applying the principles of the Well-Architected Framework, you can design Azure architectures that are secure, reliable, cost-effective, and efficient. Whether you’re building a new application or optimizing an existing one, these best practices will help you achieve your goals.
Next Steps
Complete an Azure Well-Architected Review assessment.
Azure Well-Architected Review is a self-assessment that can help a workload team examine a workload from the perspective of the Azure Well-Architected Framework. It consists of approximately 60 questions that are based on the key recommendations provided in the pillars of the Well-Architected Framework. The assessment tool can also pull in Azure Advisor recommendations for an Azure subscription or resource group.
Before initiating the assessment, it is essential to prioritize the pillars according to your specific business needs. This approach will allow you to allocate your efforts more effectively and efficiently. At the end of the assessment, you get recommendations and corresponding links to supporting material that can help you improve your workload’s design. You can export these recommendations into a file that you can use to incorporate the recommendations into the operational processes for continuous workload improvement.
When to take the assessment
For greenfield workloads, we recommend that you perform the assessment during the initial design process, entering the proposed decisions. The guidance then acts as a baseline and starts a feedback loop that you can use to refine the workload design as you make additional design decisions and periodically capture them in additional assessment milestones.
Brownfield workloads should be examined as well, as part of the continuous improvement cycle of the workload. Set a cadence, for example every four months, and use milestones to track how the workload design can continue to improve.

Receive and integrate recommendations
Assess your workload by completing the assessment. The recommendations for your current milestone are available on the assessment’s guidance page. Export these recommendations by selecting the Export to CSV button. You can use the offline copy to share the recommendations and start to prioritize them. Although some teams might consider the CSV file sufficient, we recommend that you add the recommendations to the workload’s backlog so they can be integrated into the workload’s software development lifecycle (SDLC).
Explore the Azure Well-Architected Framework documentation for more details.
Join the Microsoft Tech Community to share your experiences and learn from others.
Stay tuned for more tutorials and case studies on Azure architecture!
If you found this guide helpful, share it with your network and let me know your thoughts in the comments below. For more Azure tips and tutorials, subscribe to my blog!


